Overview
As kids, we would pull the sheets over our heads, frightened of the ghosts lurking in the shadows or the boogieman hiding underneath the bed. We have different fears as adults. The “monsters” we worry about today are cybercriminals hiding behind computer screens, stealing and encrypting vital data that causes massive disruption to business operations.
This nightmarish situation can happen quickly. In just 5 minutes and 50 seconds, a major ransomware strain known as LockBit can encrypt 100,000 files, according to Splunk. Due to the current threat landscape, protecting data at various levels is imperative.
The solution? A multi-layered security approach that intertwines each level of protection to prevent hackers from accessing various entry points and infiltrating your storage environments.
The Benefits of Multi-Layered Security
Most enterprises are using a similar technology stack to protect their network and storage systems from ransomware attacks. This includes endpoint detection, multi-factor authentication, and backups.
But you could be digging your own grave if you aren’t thinking beyond these conventional security measures.
The rise of sophisticated ransomware tactics, like double-extortion and Ransomware as a Service (RaaS), is pushing companies to adopt a multi-layered security strategy that effectively protects operations, IT infrastructure, and services. From employee cybersecurity training to developing processes like an Incident Response Playbook, it’s important to outline security measures that prevent, detect, and respond to malicious activity.
A multi-layered security strategy, like Defense in Depth (DiD), can drastically lower the likelihood of a successful ransomware attack than one with a single security solution.
A Dive into Defense in Depth
There is a lot of information associated with Defense in Depth. Let us help clear the cobwebs and simplify the strategy.
Defense in Depth is a combination of detective and protective measures with the goal of reducing and mitigating the consequences of a data breach. It’s a holistic approach that considers interconnections within an organization and utilizes existing technologies and resources to address security at every level.
According to a recent study, nearly 50% of employees have been approached by hackers to assist in ransomware attacks – emphasizing the need for businesses – large and small – to take proactive cybersecurity measures.
Picture a medieval castle. There were “layers” of defense such as a moat, drawbridge, towers, and armed knights to prevent the bad guys from seizing the treasures inside. Defense in Depth is similar. If a bad actor breaches one layer of defense, they might be contained by the next layer of defense.
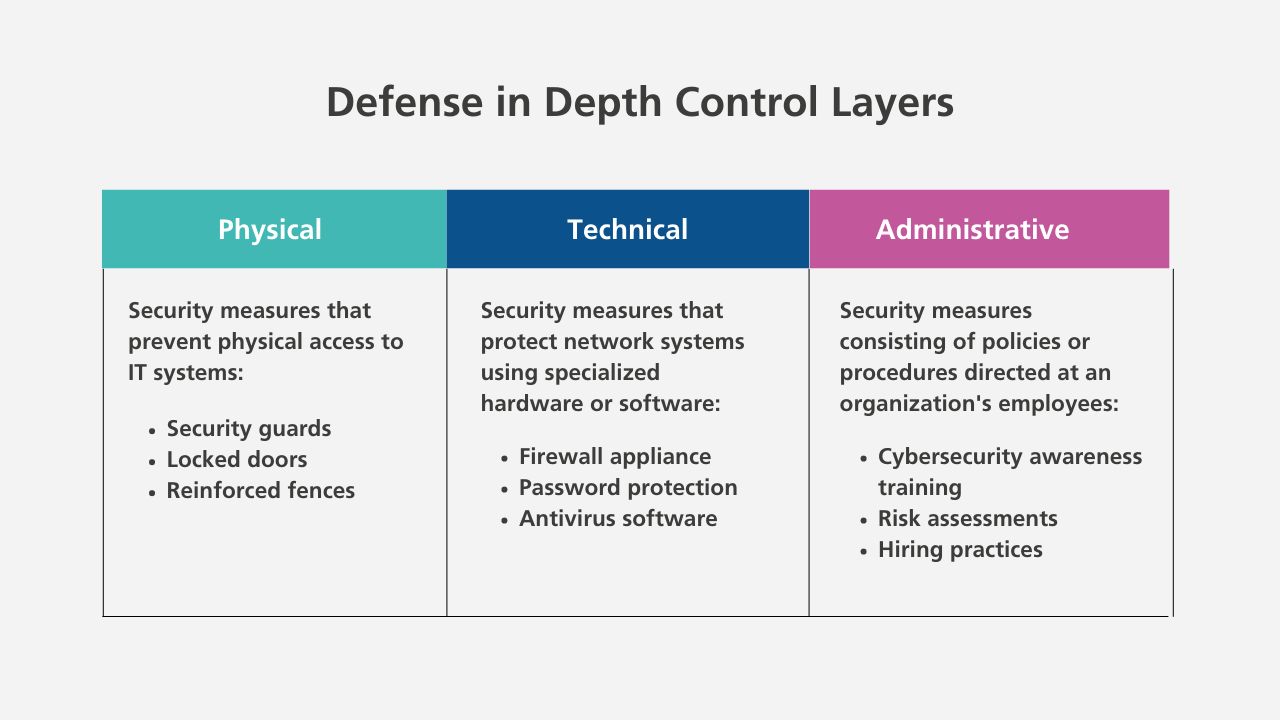
There are three control layers to protect the physical, technical, and administrative components of your network and data:
- Security measures that prevent physical access to IT systems, such as security guards or locked doors.
- Security measures that protect network systems using specialized hardware or software (i.e. firewall appliance or password protection)
- Security measures consisting of policies or procedures directed at an organization’s employees (i.e. cybersecurity awareness training or risk assessments).
Defense in Depth provides the layers necessary to optimize data security and elevate secure deployments. It’s just a matter of weaving together legacy cyber risk management solutions, such as multi-factor authentication or antivirus software, with an innovative approach to mitigating cyberattacks,
Additions to a Defense in Depth strategy include data transparency access and storage-level protection. That’s where we come in…
As you already know, speed f detection matters most when stopping ransomware from infecting your storage environments.
An added layer to your Defense in Depth strategy should be CryptoSpike, data protection software that continuously monitors all file access transactions across your data center’s storage, using behavioral analysis to automatically block all types of ransomware attacks in real time. Other benefits of CryptoSpike include:
Sleep soundly knowing your company’s sensitive information is protected around the clock, preventing the “monsters” from clawing their way into your storage environment.
