These days, hackers are no longer just encrypting your data and demanding a ransom for its return. They’re upping the ante with new tactics, like double extortion. In a double extortion attack, cybercriminals threaten to leak and sell data on the dark web. This practice has now evolved into triple and multi extortion, as ransomware gangs seek out new ways of pressurizing their victims.
Keep reading to learn how double, triple, and multiple extortion attacks work, and what you can do to protect your organization from becoming the next headline.
What Is Double Extortion Ransomware?
Double extortion is a cyberattack strategy where hackers steal the data and threaten to release it publicly. This tactic puts more pressure on victims to pay the ransom, as they face the loss of data and the potential harm of sensitive information being exposed.
Double extortion leverages the fear of reputational damage and legal consequences, making it a particularly effective and malicious form of ransomware attack.
Example of a Double Extortion Ransomware Attack
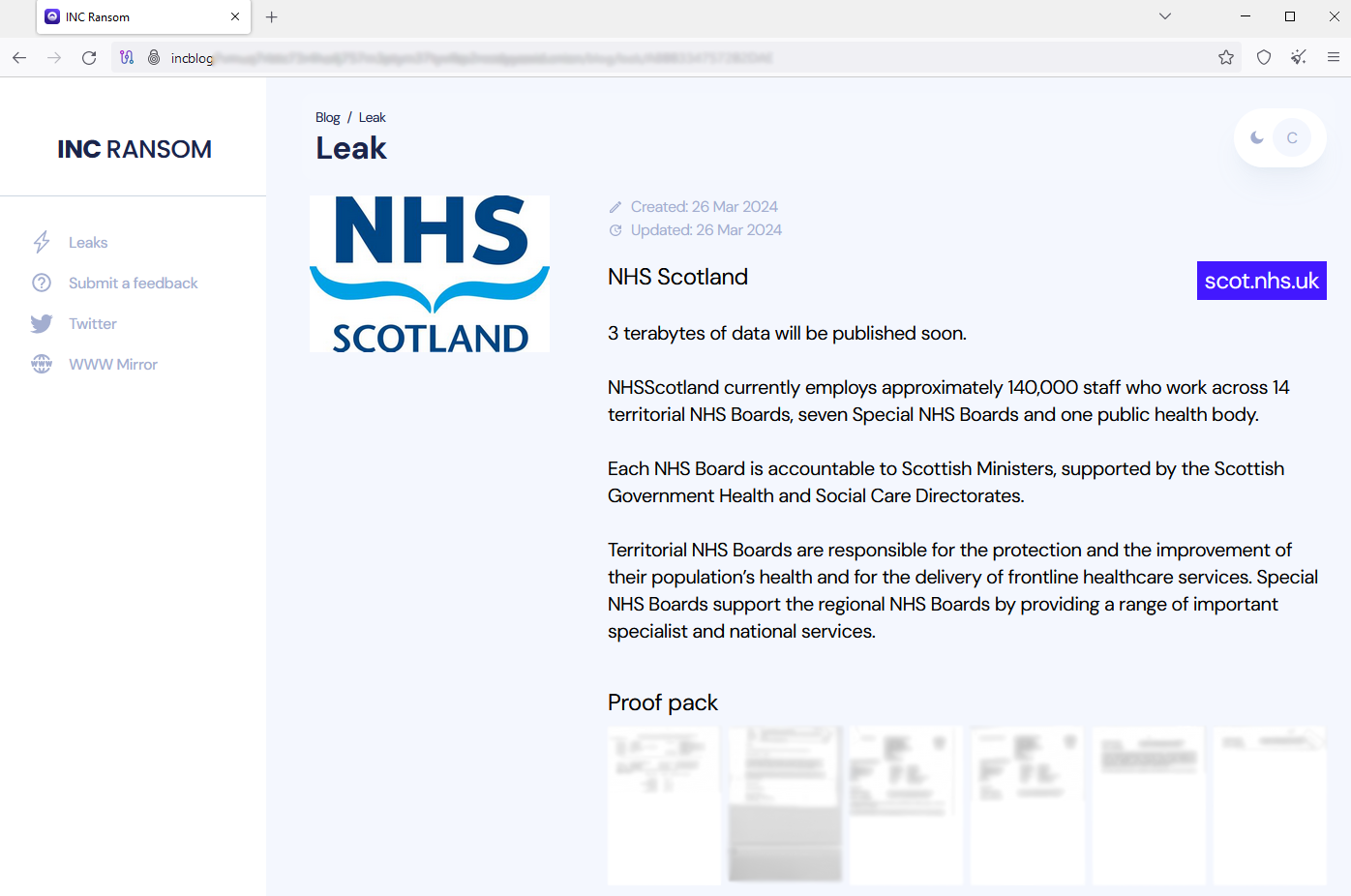
NHS Scotland
A ransomware group hacked the National Health Service in Scotland, UK, and threatened to publish three terabytes of data.
The cybercriminals published a “proof pack” of confidential information on their darknet site to encourage the NHS to pay the ransom. As the healthcare provider has access to highly confidential patient data, this is an effective tactic to force them to pay.
Source: INC Ransom extortion page (BleepingComputer)
What Is Triple Extortion Ransomware?
Triple extortion takes the double extortion ransomware attack a step further.
Hackers encrypt the victim’s data and threaten to leak it, like in a double extortion attack. Then, they might also launch a Distributed Denial of Service (DDoS) attack so the company cannot access or use its IT systems.
This approach intensifies the pressure on victims to comply with ransom demands by threatening not only their data privacy but also their operational capacity and public reputation.
Example of a Triple Extortion Attack
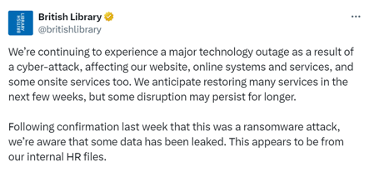
British Library
The UK’s national library was hit by a massive ransomware attack in October 2023. After they refused to pay the £600,000 ransom, the hackers threatened to auction the stolen data with a starting bid of 20 bitcoins. In the end, they leaked close to 500,000 files. What’s more, the library suffered a major outage and was offline for months.
Source: British Library X Account
Multi Extortion Ransomware
In some cases, attackers introduce a fourth layer. This involves targeting not just the primary organization but also its associates, such as customers, suppliers, or partners, with demands for ransom.
This tactic exploits the interconnected nature of business ecosystems, using the threat of secondary victimization to apply even more pressure.
The Different Phases of Ransomware Extortion
Ransomware hackers broke records in 2023, netting over $1 billion from victims. They increasingly use and combine various extortion techniques to get companies to pay up.
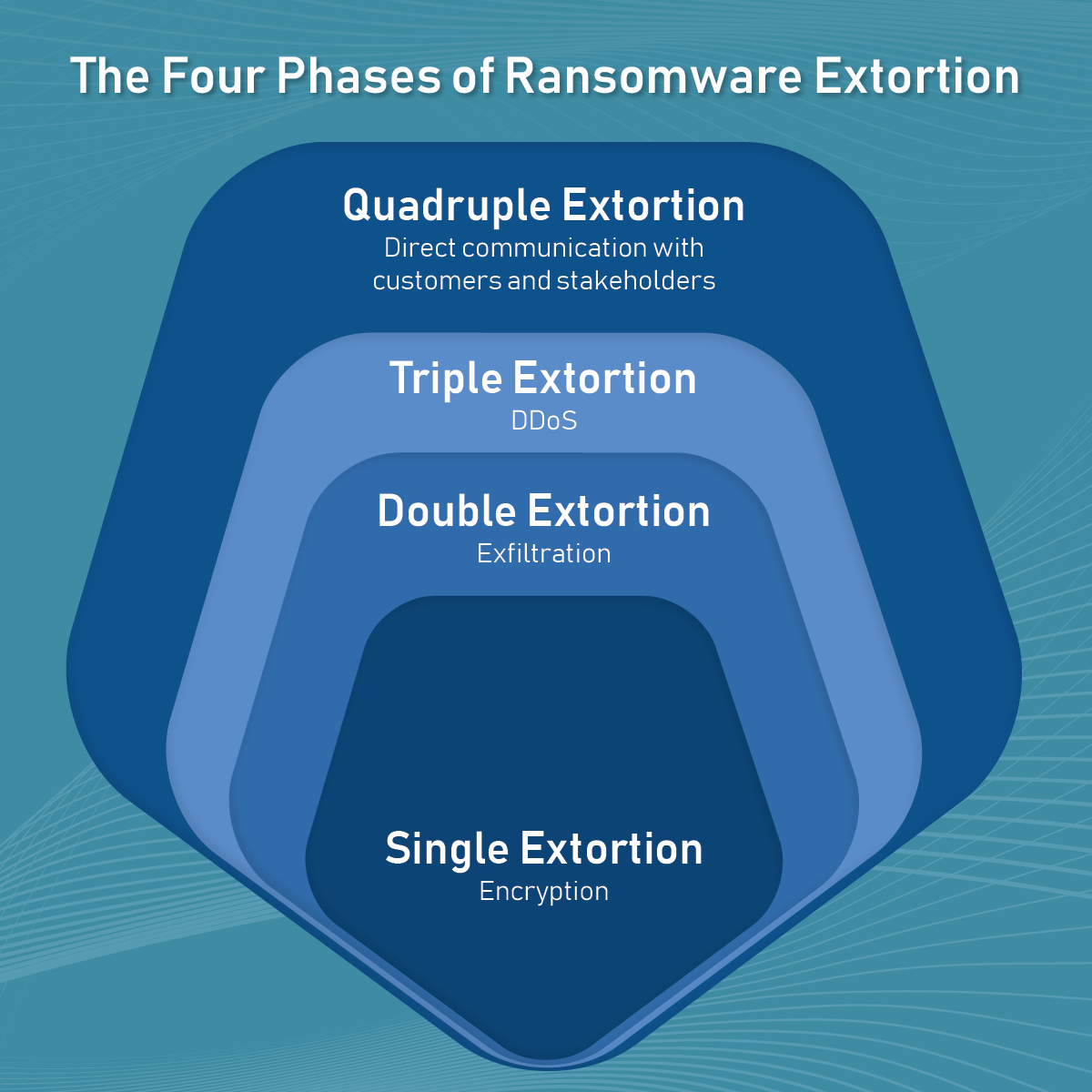
Here’s how a multi-layered attack might unfold:
Single Extortion: You realize your data has been encrypted. The hackers send you a note offering to sell you a decryption key to recover your data.
Double Extortion: You refuse to pay the ransom, so the hackers threaten to sell your data on the dark web.
Triple Extortion: Still not paying up? The hackers decide to hit your website with a DDoS attack, slowing or stopping your online operations.
Quadruple Extortion and Beyond: The hackers threaten to tell your customers, suppliers, and other partners about the breach. They might even start to threaten and demand ransoms from them, too.
Combining extortion techniques enables ransomware criminals to maximize their leverage and profits. Each layer adds another dimension of pressure on the victim.
This combined strategy has another advantage for cybercriminals: the attack can’t be solved with backups and decryption tools. Restoring your data is one thing, but the impact of a leak can be devastating.
How to Protect Against Double-Extortion Ransomware Attacks
With double-extortion ransomware on the rise, it’s clear businesses need to up their defense. Traditional security measures, like backups, won’t prevent cybercriminals from selling your confidential data. Here are some essential best practices to help you safeguard your business against these evolving threats:
- Foster Cybersecurity Awareness and Training
The human element is often the weakest link in cybersecurity. Regularly educating your employees about recognizing phishing attempts, secure password practices, and the dangers of sharing sensitive information online is crucial.
- Ensure Timely Software Updates and Patch Management
Hackers exploit vulnerabilities in outdated software to initiate their attacks. Maintaining an up-to-date IT environment by regularly updating all software and applying security patches promptly is key to shutting down these entry points.
- Embrace a Zero Trust Security Framework
The zero trust model operates on the principle of “never trust, always verify.” Do not automatically trust any request for access, even if it comes from within your network. Verify every request to minimize the attack surface and protect sensitive data.
- Craft an Incident Response Plan
Having a clear, actionable incident response plan ensures you can act swiftly and effectively in the event of an attack. This plan should outline steps for isolating the threat, communicating with all stakeholders, and restoring systems with minimal operational disruption.
- Protect Your Business with ProLion
CryptoSpike from ProLion monitors your network for signs of suspicious behavior and blocks attacks instantly. By detecting and preventing ransomware attacks in real-time at the storage level, ProLion gives organizations a last line of defense.
ProLion: Your Defense Against Multi-Extortion Ransomware
As ransomware attacks evolve from double to triple and even multiple extortion scenarios, strengthening your cyber defenses is critical. Don’t wait to become a target. Connect with a ProLion cybersecurity expert today or download our free whitepaper to learn more about the most effective ransomware protection strategies.

